iOS 14 has added a new "sandbox" security system called "BlastDoor" to iPhone and iPad to prevent attacks carried out via the Messages app. Apple hasn't released information about this new security measure, but security researcher Samuel Groß, who works with Google's Project Zero, shared his discovery.
Groß describes BlastDoor as a heavily isolated (sandbox) service that is responsible for parsing all unknown (or unreliable) data in Messages. A "sandbox" is a security service that runs code independent of the operating system and works specifically with the Messages app.
BlastDoor examines all incoming messages and inspects their contents in a secure environment, preventing any malicious code contained in a message from interacting with iOS or accessing user data.
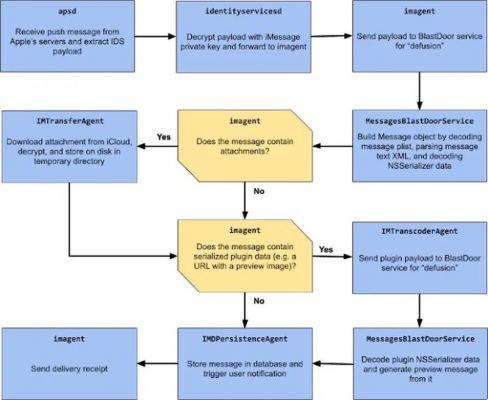
As you can see, most of the complex and unreliable data processing has been moved to the new BlastDoor service. Furthermore, this design with its more than seven services involved, allows for very specific rules to be applied, such as, for example, only the IMTransferAgent and apsd processes are required to perform network operations. Therefore, all services on this line are properly isolated (sandboxed) and the BlastDoor service is the most powerful.
This feature was designed to truncate specific types of attacks, such as those where hackers used shared cache or brute force attacks. In this sense, in recent years, security researchers have discovered vulnerabilities that allowed remote code execution in Messages that allowed to infiltrate an iPhone using only text, something that the BlastDoor implementation should eliminate.
Groß discovered this addition to iOS 14 after investigating a message hacking campaign targeting Al Jazeera reporters. The attack didn't work on iOS 14 and investigating why led him to discover BlastDoor.
According to Groß, Apple's changes to BlastDoor incorporation are "so close to optimal that they could be made taking into account [Messages's] need for backward compatibility" making the Messages platform much more secure.
It's nice to see Apple devote resources to this kind of big reprogramming to increase user-side security. Additionally, these changes highlight the value of offensive security work: not just fixing specific bugs, but making structural changes based on learning from seeing how attacks work.
If you are interested in reading the full development of how BlastDoor works, you can visit the article in Project Zero on Blastdoor.